Technology
Useful Tips: What can you do with a Rooted Phone?
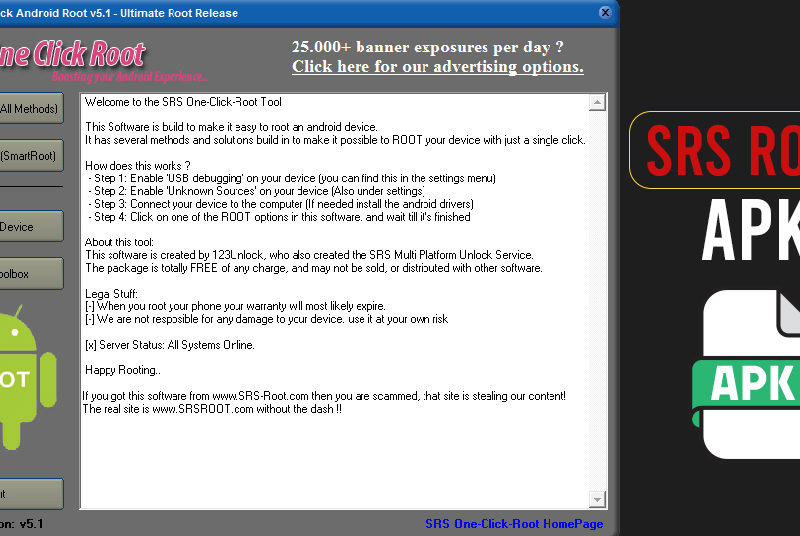
Rooting is the process of granting users of smartphone and other devices which run on the Android Read More

Root Android
Application
We know that Mozilla Firefox has the PC compatible browser, it also has the mobile version for Android and iOS platforms. Recently, Mozilla is at work
Even without using the iPhone, you can enjoy the taste of the Apple Music application on your Android devices. It is one of the most favourite music s
The hype of Players Unknown BattleGround (PUBG) is limitless. Fortnite is its greatest competitor. The game is exclusively made for mobile. A PC versi
There is a wide range of Samsung wearable gears in the market that will simply trigger your tech freak mind. These smartwatches are most appropriate f